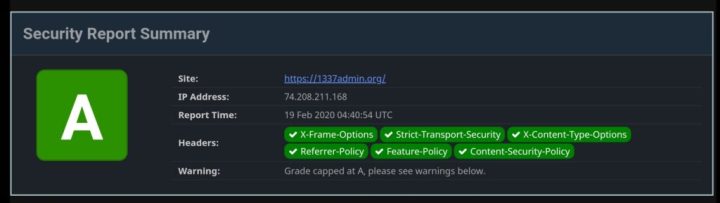
 Adding Security Headers in NGINX
Adding Security Headers in NGINX
Adding Security Headers in NGINX is simpler than you think. Just edit your website .conf file and append the following and test that it doesn’t break anything. If it does then you can use a “#” at the beginning of any line to comment it out, then test again until you find what security header is causing the issue and then look into why that feature is affecting your site or application and debug from there.
# —————————————————–
# SECURITY HEADERS – https://securityheaders.io/
# —————————————————–
# Protects against Clickjacking attacks.
# ref.: http://stackoverflow.com/a/22105445/1233379
add_header X-Frame-Options “SAMEORIGIN”;
# Protects against Clickjacking attacks.
# ref.: https://www.owasp.org/index.php/HTTP_Strict_Transport_Security_Cheat_Sheet
add_header Strict-Transport-Security “max-age=63072000; includeSubdomains; preload”;
# Protects against XSS injections.
# ref.: https://www.veracode.com/blog/2014/03/guidelines-for-setting-security-headers/
add_header X-XSS-Protection “1; mode=block”;
# Protects against MIME-type confusion attack.
# ref.: https://www.veracode.com/blog/2014/03/guidelines-for-setting-security-headers/
add_header X-Content-Type-Options “nosniff”;
# Prevents from leaking referrer data over insecure connections.
# ref.: https://scotthelme.co.uk/a-new-security-header-referrer-policy/
add_header Referrer-Policy ‘strict-origin’;
# Prevents browser features https://scotthelme.co.uk/a-new-security-header-feature-policy/
add_header Feature-Policy “geolocation ‘none’;midi ‘none’;notifications ‘none’;push ‘none’;sync-xhr ‘none’;microphone ‘none’;camera ‘none’;magnetometer ‘none’;gyroscope ‘none’;speaker ‘self’;vibrate ‘none’;fullscreen ‘self’;payment ‘none'”;
# CSP modern XSS directive-based defence, used since 2014.
# ref.: http://content-security-policy.com/
# DEFAULT# add_header Content-Security-Policy “default-src ‘self’; font-src *;img-src * data:; script-src *; style-src *;”;
add_header Content-Security-Policy “default-src ‘self’; font-src *;img-src * data:; script-src ‘unsafe-inline’ ‘unsafe-eval’ *; style-src ‘unsafe-inline’ ‘unsafe-eval’ *;”;
